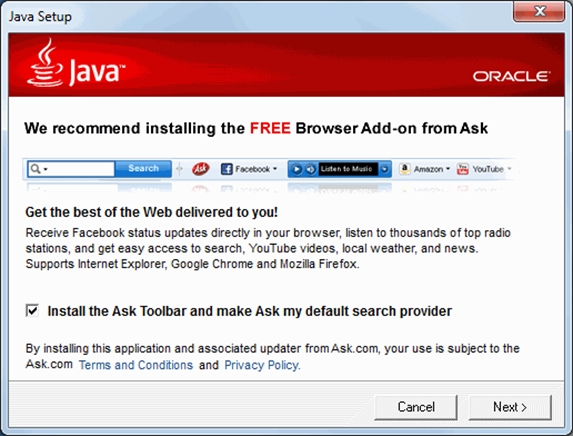
The Ask.com toolbar that is bundled with Java has been used to distribute malware in December last year. The toolbar itself is often referred to as potentially unwanted software and it's update functionality had been exploited by cybercriminals to infect users with malware.
Also in November last year a similar incident took place and also this time malicious updates were distributed.
Normally, the Ask.com toolbar only accepts updates that are signed with a certificate of the developers. Both in November and December, criminals compromised the update process and had their own malicious update signed with the Ask.com certificate.
The malicious update contained a so-called dropper/uploader which in its turn downloaded malware. The criminals used different types of malware, likely to see what worked the best. Because the Ask.com toolbar runs with full privileges, the malware has full rights on the computer.
On infected systems the attackers mapped the local network and gained access to the login and passwords of users. It also installed a hard-to-find/obfuscated remote access tool, so the system would still be accessible by the criminals, even after the actual malware was cleaned.
Users are adviced to remove the Ask.com toolbar, this can be done in the Windows Control Panel under 'Uninstall a program'.