The number of malicious advertisements that try to infect internet users with malware has gone down considerably lately and is likely the result of the disappearance of the Angler exploit kit. The Angler exploit kit was previously the most used tool by cybercriminals to infect users using known vulnerabilities in Adobe Flash Player, Internet Explorer and Silverlight.
Internet users were infected when they used outdated versions of the mentioned software and visited a website serving the Angler exploit kit or viewed an advertisement that redirected the user to a page serving the kit. The exploit kit infects computers without any user interaction.
Angler was the most popular exploit kit for cybercriminals the last two years and was used on large scale to infect internet users around the world. Since the beginning of June the exploitkit suddenly disappeared and didn't return.
Since then no large scale attacks using malicious advertisements have been reported, according to Jerome Segura from Malwarebytes. Other exploit kits such a RIG of Magnitude are now used to infect users with malicious advertisements but their scale and sophistication can't be compared to the Angler exploit kit.
"Malvertising has always come in waves with attackers calculating their next move and big target, but the apparent demise of Angler EK has had an immediate impact", according to Segura.
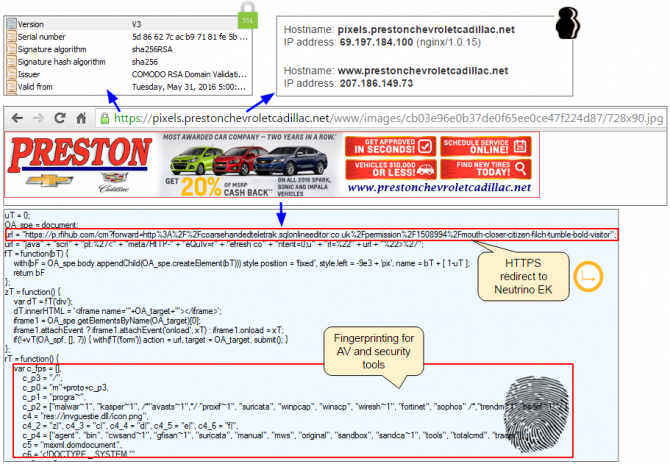
The Neutrino exploit kit is now the most used kit, and is mainly used to infect users through hacked websites.
"It is far easier to hack into regular websites and inject malicious code but the reach in terms of traffic is much smaller compared to having a malicious advert displayed on top tier publishers. A single bad ad can expose hundreds of thousands of people at once, whereas it would take a lot of compromised websites to reach the same exposure level", Segura explains.