Microsoft warns for an increase in attempts to distribute the Cerber ransomware in the recent months. The latest version of this malware not only encrypts files but also searches in more folders for files.
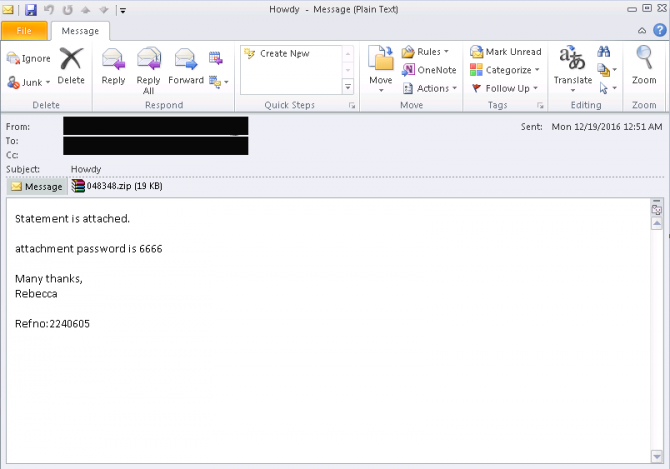
Cerber is one of the most active ransomware variants and spreads through email attachments and drive-by downloads. Especially European internet users are attacked through an old vulnerability in Adobe Flash Player. This is a vulnerability that Adobe patched last December. In case of the email attachments a password protected ZIP file is used. These compressed file contains a Word document with a malcious macro. When the macro is enabled, it will install the Cerber ransomware. In its turn, Cerber will encrypt all files.
The developers of Cerber also continue to improve their malware, to both evade virus scanners and to increase the complexity. They've added new methods of obfuscating their source code, improved the encryption of their configuration files and new IP ranges for command and control servers were added.
The latest version also adds 50 new file extensions to encrypt and several other file extensions are removed from the encryption list like .EXE, .CMD, .BAT and .MSI. Other ransomware already did this but it's the first time Cerber does too.
The ransomware now also searches for Microsoft Office folders to encrypt files.
"It is important to note that one of the most critical updates in this latest version of Cerber is the new folders it prioritizes during encryption. The added folders, which include microsoft\onenote, microsoft\outlook, and \microsoft\excel\ among others, is further indication that the malware is designed to look for critical Office files to encrypt in enterprise environments," Microsoft writes.