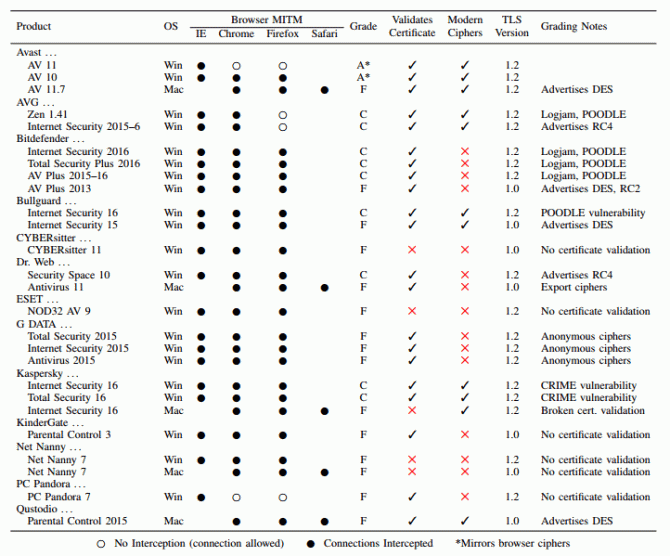
Google, Mozilla, Cloudflare, and researchers from two Universities have criticised the interception of HTTPS traffic by antivirus software. According to the researchers and companies this has far-reaching consequences for the safety of users and their internet connection.
By default it's not possible for antivirus software to access HTTPS traffic. By installing an own root certificate on the user's computer the antivirus applications have found a way to be able to analyze the content of encrypted internet connections. This method is frequently used by antivirus vendors. However, the way the software intercepts HTTPS traffic decreases the security of it. Even worse, the virus scanners introduce all kinds of new vulnerabilities, according to a report released by the researchers and companies.
For the report, the researchers analyzed 8 billion secured connections to the Firefox update servers, to several popular e-commerce websites and to Cloudflare's content distribution network. About 4% of the connections to the Firefox servers was intercepted, 6.2% of the e-commerce websites and 10.9% of the connections to Cloudflare was intercepted.
The researchers also analyzed the security impact of the intercepted connections. About 97% of Firefox, 32% of e-commerce, and 54% of Cloudflare connections that were intercepted became less
secure.
"Alarmingly, not only did intercepted connections use weaker cryptographic algorithms, but 10–40% advertised support for known-broken ciphers that would allow an active man-in-the-middle attacker to later intercept, downgrade, and decrypt the connection," according to the researchers.
While it was already known that security software intercepted HTTPS traffic, the researchers were still surprised, "while the security community has long known that security products intercept connections, we have largely ignored the issue, believing that only a small fraction of connections are affected. However, we find that interception has become startlingly widespread and with worrying consequences."
Thy hope that security vendors will start using alternatives to HTTPS interception as, "interception products drastically reduce connection security."