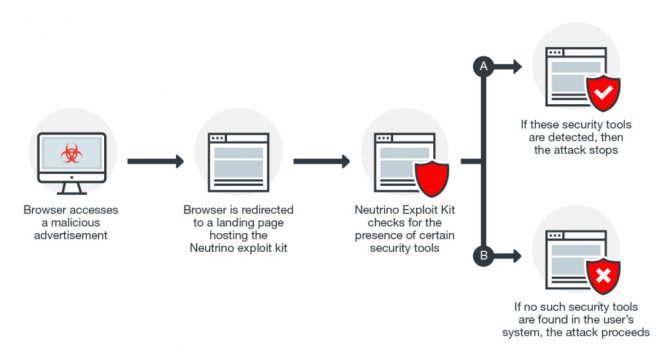
Antivirus company Trend Micro reports that a zero-day leak in Windows, which was patched this month, has been actively attacked with malcious advertisements in July last year. The vulnerability, that was reported to Microsoft in September last year, allowed an attacker to access information about files on the victim's computer.
This way attackers were able to determine which security software was installed or whether the computer had software installed to analyze malware. It also allowed attackers to check whether the attacked systems ran sandbox software or had packet capture software installed. If this kind of software was detected the attackers didn't execute their malcious code and it remained hidden for security researchers.
The zero-day vulnerability was privately reported to Microsoft by Trend Micro and existed in Windows versions from Vista SP2 and onwards. Visiting a specifically prepared website or advertisement could lead to infection.
Initially the zero-day vulnerability was used by a malvertising campaign called AdGholas that used infected advertisements to infect internet users with malware. Later it was also added to the Neutrino exploit kit.
The vulnerability itself was not sufficient to infect computers with malware as it only checked for the presence of security software.For the actual infection a second vulnerability was required, in case of the Neutrino exploit kit these were known vulnerabilities in Adobe Flash Player.