Cybercriminals have silently changed the DNS server of more than 100,000 routers around the world. By changing the DNS, the criminals are able to redirect all internet traffic of victims through their servers. This allows them to e.g. serve phishing sites to obtain sensitive data or steal money from online banking accounts. Affected routers include brands like D-Link, MikroTik, TP-Link, Huawei and SpeedTouch.
Attacks where criminals attempt to change the DNS server of routers are not new. However, from the 20nd of September of this year a large attack was discovered by security researchers.
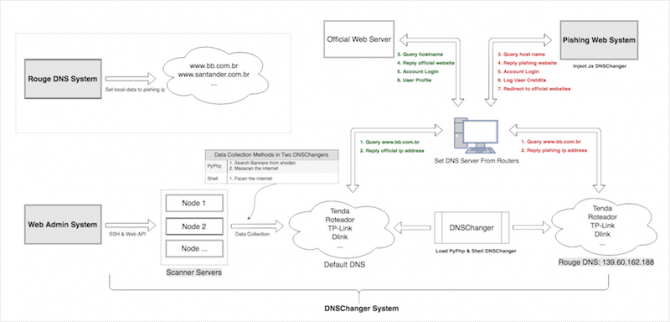
For the victim the attack starts when visiting a malicious website which contains a script that is executed on the computer and that checks whether specific router ports on the internal network are open. After that, the script tries to login to the router administration area by brute forcing (making numerous automated guesses) the password. Many users use the default username and password which makes them extra vulnerable. Once the criminals are able to login they change the DNS server address of the router.
The Domain Name System (DNS) works like a phone book, it converts domain names to an IP address. When the DNS server of the router is changed to one under control of criminals, victims don't receive the IP address of the actual site but any IP address the criminals want. This way they can redirect users to phishing sites, while totally unnoticeable to the victim.
The current attack, discovered by network security lab 360 Netlab, affects more than 70 different routers:
- 3COM OCR-812
- AP-ROUTER
- D-LINK
- D-LINK DSL-2640T
- D-LINK DSL-2740R
- D-LINK DSL-500
- D-LINK DSL-500G/DSL-502G
- Huawei SmartAX MT880a
- Intelbras WRN240-1
- Kaiomy Router
- MikroTiK Routers
- OIWTECH OIW-2415CPE
- Ralink Routers
- SpeedStream
- SpeedTouch
- Tenda
- TP-LINK TD-W8901G/TD-W8961ND/TD-8816
- TP-LINK TD-W8960N
- TP-LINK TL-WR740N
- TRIZ TZ5500E/VIKING
- VIKING/DSLINK 200 U/E
In total more than 100,000 routers are affected by the attack of which the majority is located in Brazil. As soon as the users browse to specific websites they are redirected to phishing sites. These include online banking sites but also Netflix and hosting companies.
Users are advised to make sure the firmware of their router is up-to-date, to set a strong password on the admin area of the router and to regularly check their DNS settings. Meanwhile, several hosting companies that hosted phishing sites used in this attack, have blocked the IP addresses used by the criminals.
Last week we also reported that an American consumer organization found that 83% of the home and office routers contained serious vulnerabilities.
















