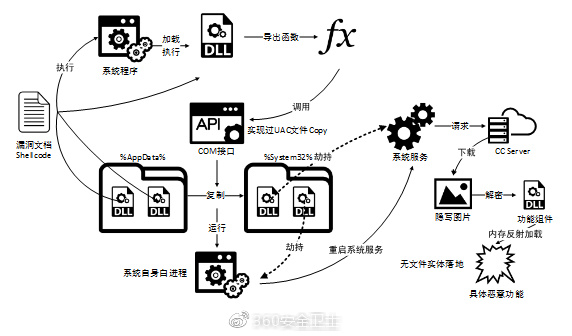
Antivirus vendor Qihoo 360 reports it has found a zero-day vulnerability in Internet Explorer that is actively exploited and for which no patch from Microsoft is available yet. The company announced the vulnerability on Twitter and provides more details on the Chinese social network Weibo.
According to Qihoo 360, the vulnerability is attacked through Microsoft Office documents that contain an embedded web page. Simply opening the malicious Office document is sufficient for a malicious payload (e.g. a trojan) to be loaded from a remote server. This allows attackers to take full control over the system. The attackers use stenography and 'file less' downloads to hide their attack. The vulnerability exists in the latest version of Internet Explorer, but also software that uses the IE kernel is vulnerable.
We uncovered an IE 0day vulnerability has been embedded in malicious MS Office document, targeting limited users by a known APT actor.Details reported to MSRC @msftsecresponse
— 360 Threat Intelligence Center (@360CoreSec) April 20, 2018
The attackers make use of a known method to circumvent the Windows User Account Control (UAC) feature. UAC limits applications to standard user privileges until an administrator authorizes an increase or elevation. The method utilized by the attackers allows them to elevate their rights.
Qihoo 360 has informed Microsoft about the vulnerability but the software has not responded (publicly) so-far.