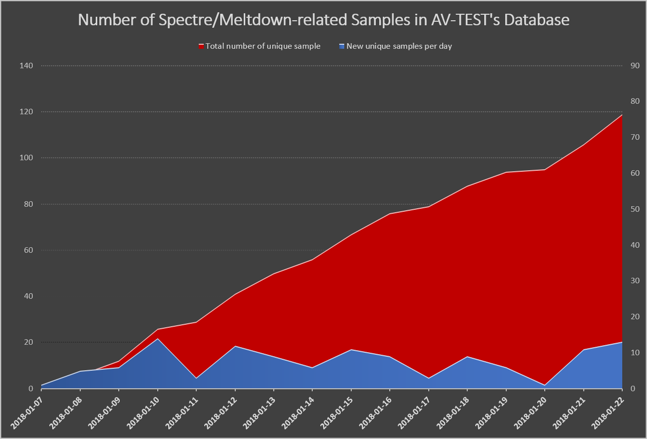
AV-Test discovered 119 malware samples last month that can be associated with the Spectre and Meltdown attacks. Since the vulnerabilities were revealed last month, no attacks 'in the wild' have been discovered yet by the German test lab.
The majority of the malware discovered by AV-Test is based on 'proof-of-concept' code from the researchers who disclosed the Spectre and Meltdown vulnerabilities, according to security company Fortinet. With the proof-of-concept code, the researchers demonstrated how the Spectre attacks makes it possible to steal data from the browser's memory using malcious Javascript code. Also through Meltdown it's possible for malware to retrieve data in the computer's memory that it normally should not be able to retrieve.
Fortinet's researchers analyzed 83% of all samples. Which means there are some samples untested. Fortinet explains how that's possible, "the other 17 percent may have not been shared publicly because they were either under NDA or were unavailable for reasons unknown to us".
The Dutch website security.nl asked AV-Test for more details on the discovered 119 samples. They received a reply from Andreas Marx from AV-Test who reports that meanwhile 139 samples have been found. The majority of them are re-compiled or extended versions of the proof-of-concept code.
"Interestingly, the samples were available for different platforms like Windows, Linux and macOS. We also found the first Javascript proof-of-concept code for browsers like Internet Explorer, Chrome or Firefox", Marx reports.
The malware comes from several sources like other researchers and testers but also from other antivirus vendors.
"I think different groups work on proof-of-concepts to determine whether they can use them somehow", Marx continues. Given the large amount of vulnerable systems, Spectre and Meltdown are interesting for cybercriminals to steal data from browsers.
"I'm confident that we're still in the research stage of the attacks, but I wouldn't be surprised if we see the first targeted attacks in the future", according to Marx.
Large attacks depend on how easy it is to perform the attacks. Marx advices users to update their BIOS and OS and to turn off their computer if it's not used for a while. Not only does it reduce the attack surface but it also saves energy.