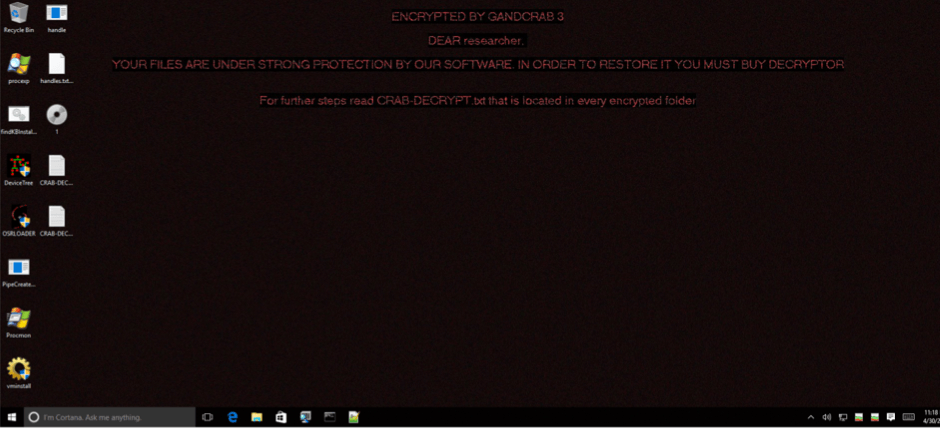
Researchers warn for a new ransomware variant that breaks the Windows 7 boot process due to a bug in the malware. The ransomware has been discovered by security researchers from the cybersecurity company Fortinet.
The ransomware is a new variant of the GandCrab, which is distributed through email attachments. As soon as the attachments are opened, the ransomware starts to encrypt all kinds of files. It also changes the desktop background to an image that contains instructions on how the files can be decrypted. After that, the system is rebooted.
However, on Windows 7 the reboot doesn't properly finish. The system is stuck at the point where normally the Windows Shell loads, only the desktop background image with the instructions is visible. The user of the infected system can't use the Windows GUI which makes it appear that the system doesn't work.
This is not how the developers of the ransomware intended it to work, but due to a bug, as Fortinet explains, “we know this wasn’t intentional because the instructions on the ransom note tells the user to read a copy of one of the“CRAB-DECRYPT.txt” ransom notes scattered around the system for further instructions. And for the average user, that would at least require the Windows interface to do it.”
Because the ransomware starts itself, also a new reboot will cause Windows not to fully load. Fortunately there is a workaround, through the Task Manager and Windows Registry, users can stop the ransomware. “Although for an average user, finding an actual malware from the list of running processes can be a complicated undertaking,” according to Fortinet researcher Joie Salvio.
Bugs in malware are not new, just like in regular software, they are also frequently found in malware.