A company that develops flight simulator add-ons has added a tool to pirated versions of its software that is able to steal passwords from Chrome. The tool was discovered when several antivirus scanners detected it as 'risk ware'. According to the company the tool is part of the software's DRM.
The developer of the flight simulator add-ons is the company FlightSimLabs. On its support forum the company stresses that the tool has only been added to pirated versions of their software.
“There is a specific method used against specific serial numbers that have been identified as pirate copies and have been making the rounds on ThePirateBay, RuTracker and other such malicious sites,” according to Lefteris Kalamaras, the CEO of FlightSimLabs in a post on the company's forum.
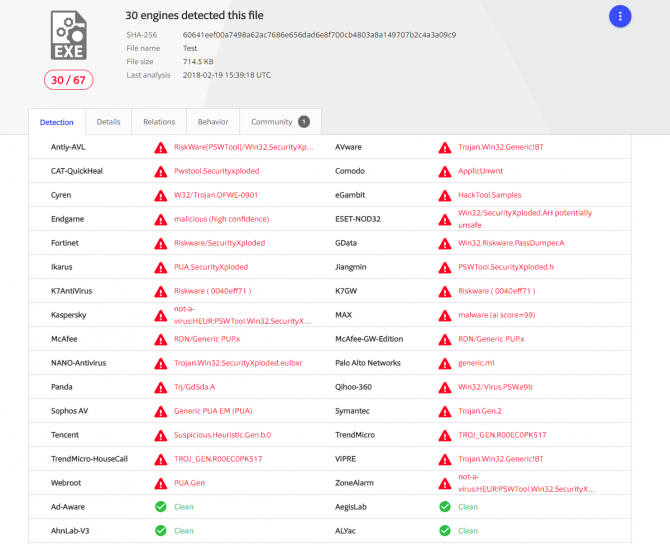
The tool, test.exe, was discovered after a Reddit user used Virustotal to scan an installer from the A320X software from FlightSimLabs. Virustotal is an online virus scanner that uses engines of pretty much all known antivirus products. In this case, 30 of the 67 antivirus engines detected so-called 'risk ware' in the installer. More specifically, the engines report they found SecurityXploded, marketed as a 'password recovery tool'. In reality, it means it can dump password stored in Google's Chrome browser.
Kalamaras doesn't explain why SecurityXploded is part of the installer, other than that it's part of the DRM. In the forum post he writes, “this method has already successfully provided information that we're going to use in our ongoing legal battles against such criminals.”
This indicates that pirated installers of software from FlightSimLabs try to steal passwords from users who illegally use the software. Obviously, those users can have all kinds of passwords saved in Chrome, ranging from company sites to email accounts. With the collected passwords, FlightSimLabs could log in to those accounts and obtain personal data.
Although it's not obvious, if and how, the stolen passwords are used to catch those pirates, the forum post makes clear that the company bundled SecurityXploded purposely and that the tool is somehow used in legal battles against software pirates.
It rather unorthodox to steal browser passwords from software pirates, as also Kalamaras understands, “we will be happy to provide further information to ensure that no customer feels threatened by our security measures - we assure you that there is nothing in our products that would ever damage the trust you have placed in our company by being our customer.”
Meanwhile, the company also made an installer available that doesn't contain SecurityXploded.