A group of cybercriminals has started 28 fake advertising agencies to distribute malicious advertisements that tried to infect internet users with malware. To keep up appearances, and to make their companies look more genuine, the criminals created fake LinkedIn profiles of their non existing CEOs.
Security researchers from Confiant analyzed their behavior and named the group of cybercriminals, “Zirconium”. Criminals in the group were involved in both attracting traffic and creating malicious landing pages.
The fake advertising agencies built up relationships with legitimate advertising platforms to purchase traffic. Traffic purchased by the group was resold to so-called affiliate platforms, like Voluum and AdSupply that are known for their, “leniency towards malicious campaigns”, according to Confiant.
Other cybercriminals could use Zirconium to sent traffic to their malicious landing pages. Later the group launched its own advertising network called “MyAdsBro”. The network was used to distribute their own malicious advertisements. These advertisements sent users to malicious website that offered fake Flash Player update, which, in reality, was malware.
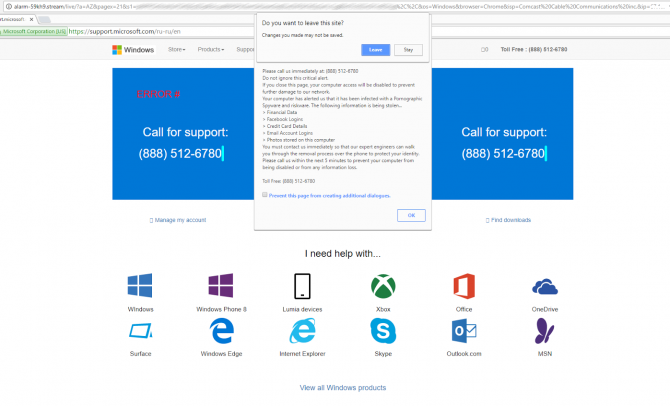
Internet users were also directed to websites that claimed their computer was infected and that users had to call the phone number that was listed on the website. When users called the number, they were connected to scammers that pretended to be Microsoft support employees.
Confiant estimates that the group has displayed 1 billion advertisements. To not attract too much attention, only a small percentage of the advertisements directed users to malicious websites.
Twenty of the Zirconium owned advertising agency are no longer active. The other eight were never actually used.