Now that Google marks the use of non-encrypted HTTP websites as unsafe in Chrome 68, there are likely many people that will falsely assume a website is fine if the address bar does not say “not secure”. One very good example is a phishing website, such as from a fake security related e-mail.
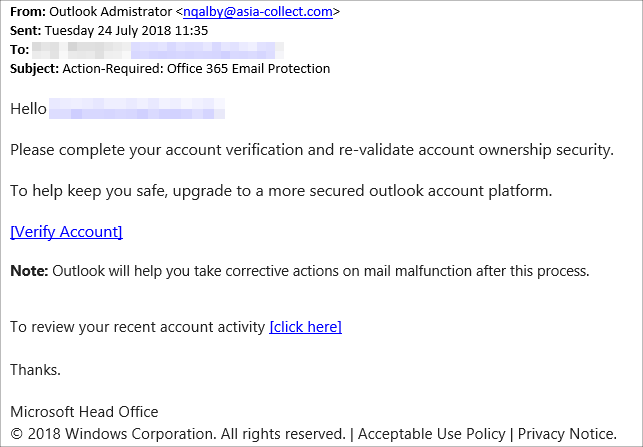
To demonstrate this and to also show just how ineffective Internet security products can be at identifying phishing, let’s consider the following e-mail I received today. This phishing attempt targets Office 365 users:
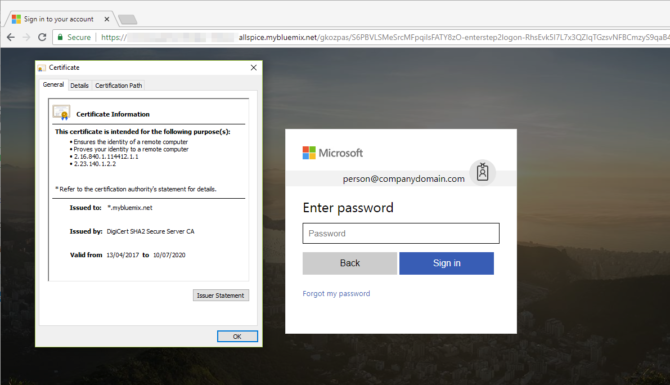
For anyone familiar with phishing e-mails, the 'From:' e-mail address and the URL shown when hovering the links are clear indicators that this is phishing bait. However, for a complete newbie to phishing that clicks the link, it brings up the following page, for which we also display the security certificate:
Notice the green ‘secure’ indicator at the top-left. This green 'Secure' means nothing more than that the connection between the user's browser and the server is secure against eavesdropping. It does not necessary mean that the website is safe and the above is just one example of a phishing website using HTTPS.
At the time of testing, Edge, Chrome and Firefox all loaded that Office 365 phishing webpage without any warning. Both Symantec Cloud Security and MalwareBytes Premium (3.5.1) did not detect anything suspicious either. From a quick look at the certificate, it is using a DigiCert certificate, which would have been purchased, unlike Let's Encrypt. This means that it's likely some organisation is unaware that its website has been compromised and now hosts malware to serve this phishing webpage.
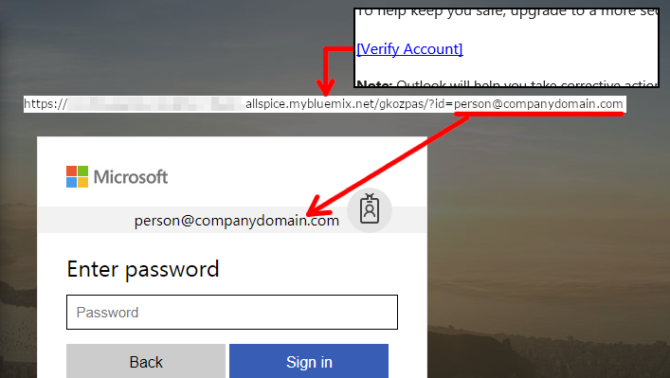
In the above phishing e-mail example, the [Verify Account] link had the recipient’s e-mail address at the end of the link it points to. I replaced the e-mail address with this factitious e-mail address to demonstrate how the phishing website uses the e-mail address to give a false impression that the user was there before:
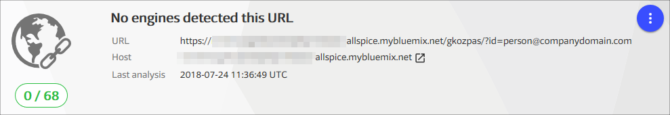
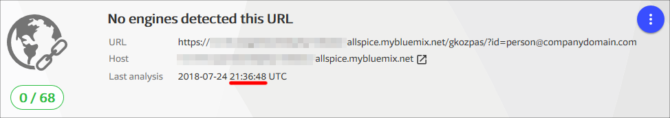
With Microsoft, Google, Symantec and MalwareBytes not detecting the phishing link, it made me wonder whether any other Internet security product detects the link. According to VirusTotal, not one product engine detected the URL at the time of receiving the phishing e-mail:
As the URL contains the recipient’s e-mail address, the VirusTotal community rating will always be zero as each person receives a unique URL. For example, when I tried marking the URL as unsafe and looked up the URL with a different e-mail address at the end of the URL, VirusTotal showed the community rating as zero again.
At the time of receiving the e-mail, I used the “Report Unsafe Website” link in Edge and in Firefox, which uses Google’s Safe Browsing. I retested the link 10 hours later and Edge, Chrome and Firefox still had no issue loading the phishing website. As for the Internet security products, not a single product detects the URL at the time of publishing according to VirusTotal, 10 hours after receiving the phishing e-mail:
What is clear is that the only way for people to avoid phishing is to learn and become familiar with how to identify phishing e-mails and websites. An example would be training for new employees before they can receive external e-mails.
Finally, it is worth noting that 2-factor authentication is also ineffective at preventing phishing. If an unsuspecting victim tries logging into a phishing website and receives a “Approve logon” request on their mobile device, they are obviously going to touch ‘Allow’, unaware that this is a phishing scam.