Cybercriminals distribute emails with files attached in a specific Linux/Unix compressed file format. By using that format they are able to bypass Windows security warnings and infect systems with malware. The attack was discovered by Belgian security researcher Didier Stevens.
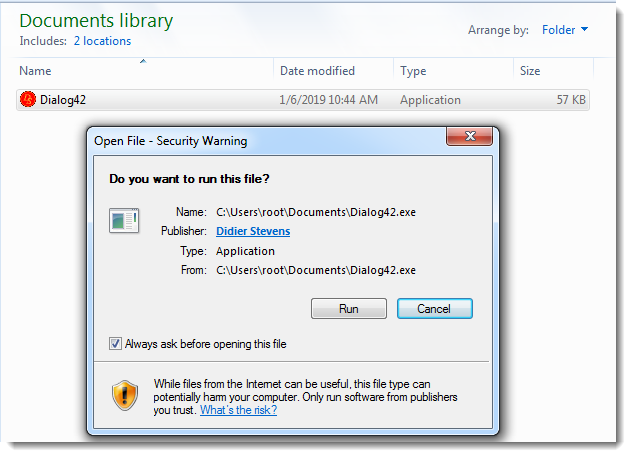
The specific compressed file format is .TAR and Windows users are unable to unpack TAR files by default. It's however possible to unpack .TAR files with a file archival application such as WinRAR or 7Zip. For attackers this is partly a disadvantage, as a user needs to have special installed, but it also has an advantage. Windows normally marks files that are downloaded from the internet as “mark-of-the-web”, but it doesn't mark files that originate from an unpacked file.
Applications like Outlook also adds the mark-of-the-web to attachments when they are opened or saved. However, when a .TAR file is unpacked, the resulting file doesn't have the mark-of-the-web. Users who then execute the resulting file, therefore don't see a security warning.
Besides .TAR, the attackers also use other compressed and/or archival formats such as .ISO, .JAR and .ARJ.
“Using less popular container formats on Windows allows malware authors to evade detection and reduce the number of alerts, at the risk of ending up on a Windows machine that can not open the container”, Stevens explains.
















