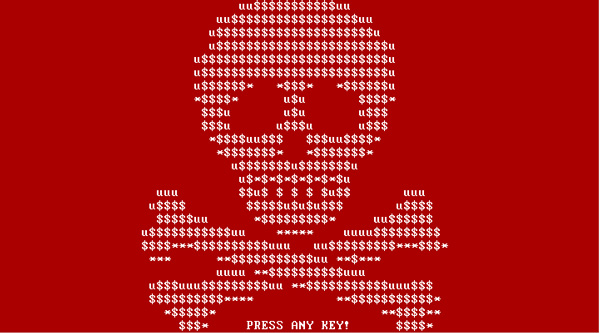
The Petya ransomware which makes HDDs inaccessible all over the world has been cracked by a security researcher. By entering some information on a website the HDD can be made accessible again. Petya was first discovered last month and encrypts the Master File Table (MFT) which makes the filesystem unreadable and prevents Windows from starting.
Distribution of the ransomware goes through emails to companies with a link to a file Dropbox. If the file is opened the computer crashes, automatically reboots and then shows a notification that the computer performs a disk check. In reality this is when the ransomware performs its nasty job, it encrypts the MFT.
Security researcher Leo Stone has found a solution and developed an algorithm that generates the key which can decrypt the MFT. The algorithm only takes a couple of seconds to retrieve the key. Because the encryption is based on several parameters of the HDD these have to be extracted. A simple tool developed by Emisoft developer Fabian Wosar is able to retrieve this after which the data can be entered on Stone's website to retrieve the decryption key.
A full explanation can be found here.